Securing the Internal MQTT broker
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. It uses public-key cryptography to provide authentication, and secret-key cryptography with hash functions to provide for privacy and data integrity.
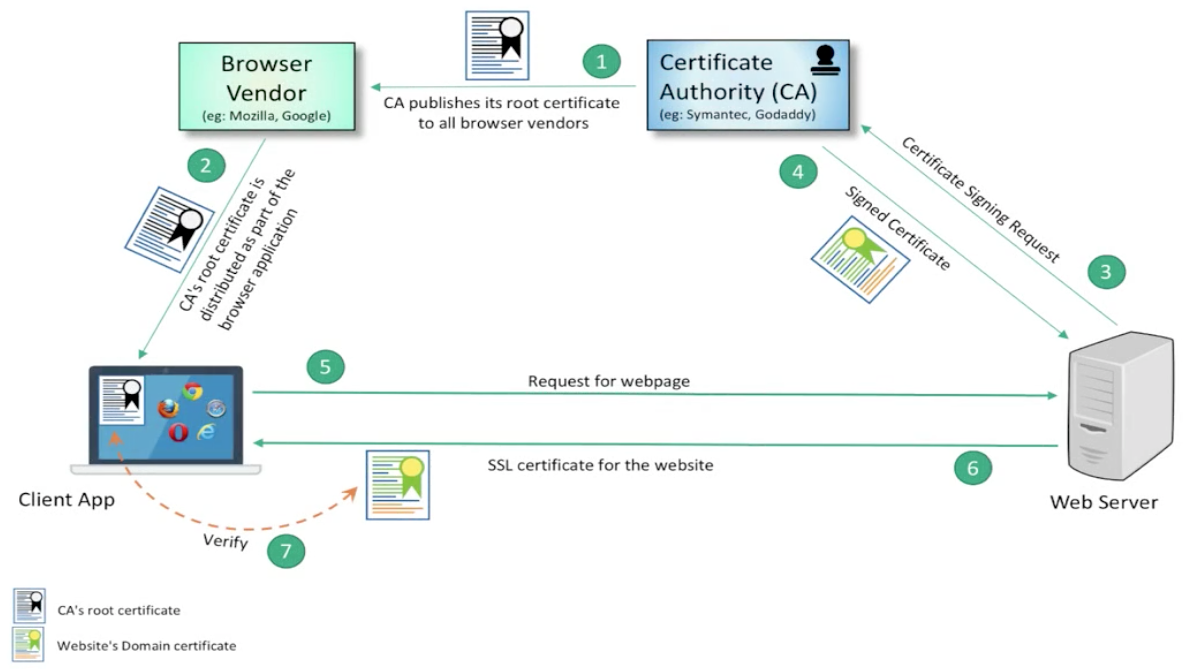
SSL Record Protocol
SSL Record Protocol provides two services to the connection:
-
Confidentiality. This encrypts data fragments using Master Secret
-
Message Integrity. This adds Message Authentication Code to each data fragment
TLS with Edge Xpert Message Bus
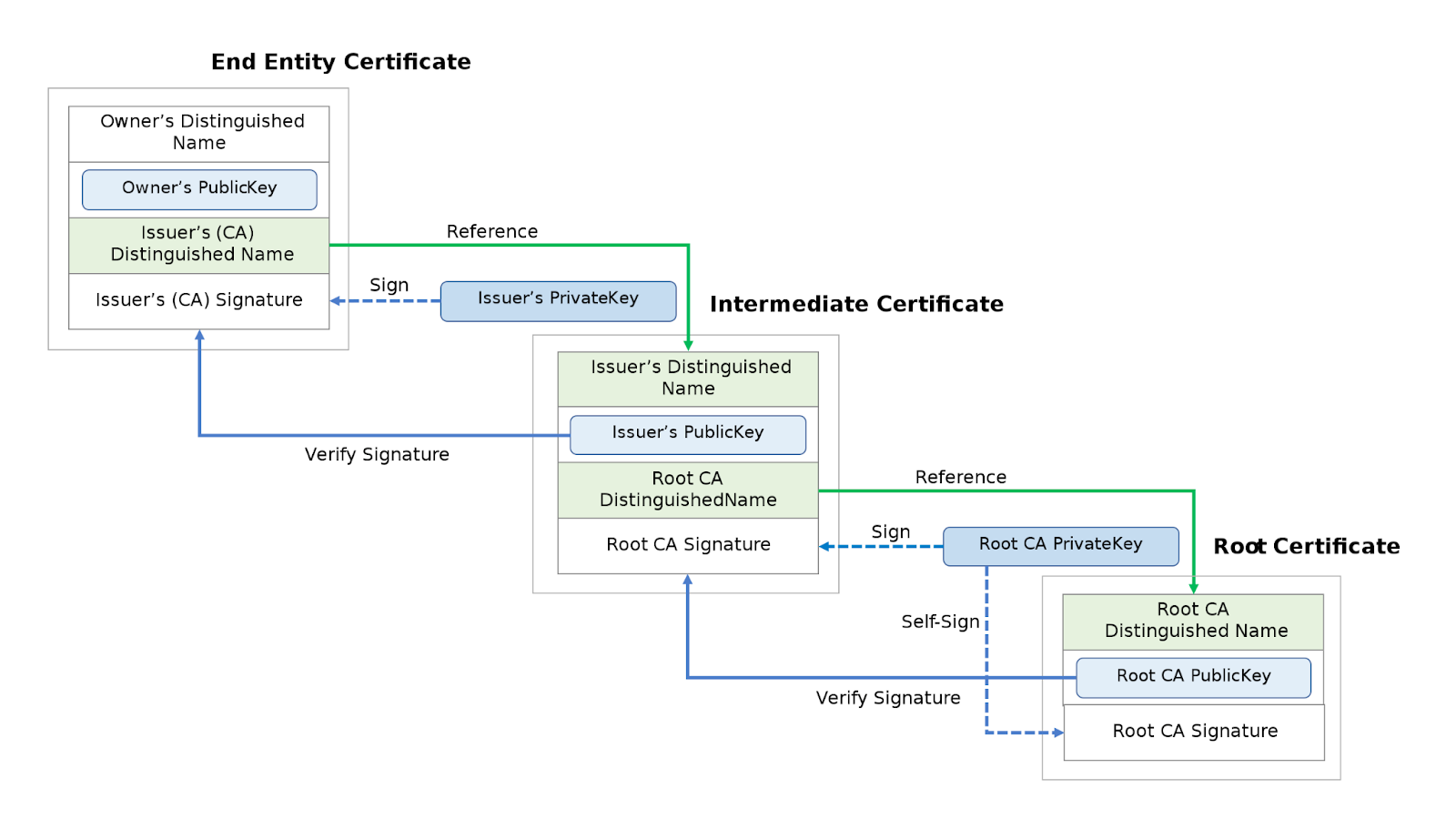
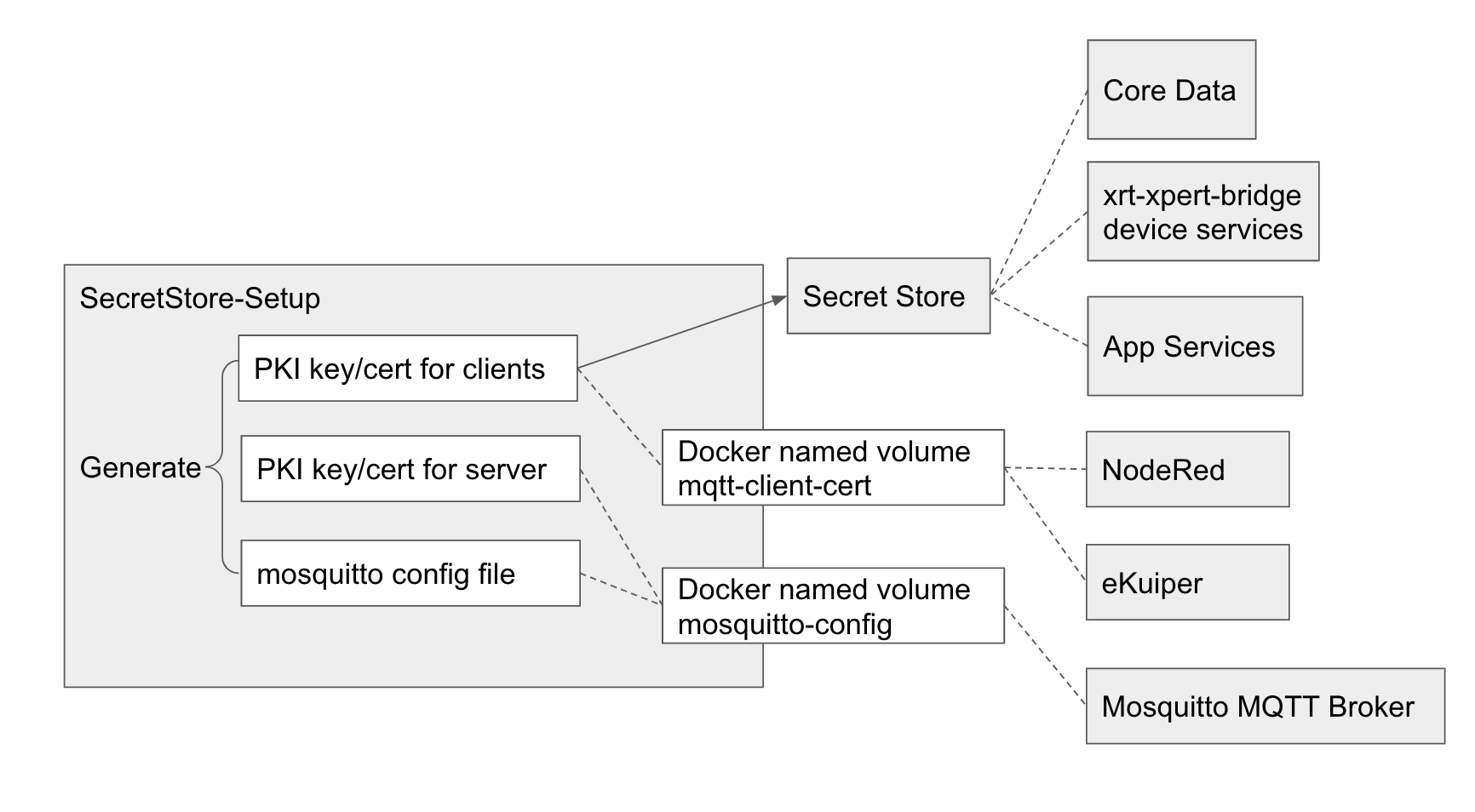
In Edge Xpert, the CA certificate is created and signed by the SecretStore-Setup, itself using the OpenSSL utility.
To enable TLS on the internal MQTT broker (Mosquitto), a Mosquitto configuration file and a set of keys and certificates are required. SecretStore-Setup microservice is responsible for creating these and sharing them with the MQTT broker and other Edge Xpert services over a Docker named volume or SecretStore.
Enable TLS on the Edge Xpert Message Bus
By default, the internal MQTT broker has no TLS enabled.
To use TLS-enabled mqtt-broker as the internal message bus, set the following environment variables on the host before executing edgexpert up --secret:
export EDGEXPERT_MESSAGEBUS_MQTT_TLS=true
export EDGEXPERT_MESSAGEQUEUE_PROTOCOL=tcps
export EDGEXPERT_MESSAGEQUEUE_PORT=8883
export EDGEXPERT_MESSAGEQUEUE_AUTHMODE=clientcert
Additionally, if the Application Service is configured to use the default Edge Xpert Message Bus (mqtt-broker) and is to be launched by Edge Xpert CLI, the following environment variables are also required:
export TRIGGER_EDGEXMESSAGEBUS_SUBSCRIBEHOST_PROTOCOL=tcps
export TRIGGER_EDGEXMESSAGEBUS_SUBSCRIBEHOST_PORT=8883
export TRIGGER_EDGEXMESSAGEBUS_PUBLISHHOST_PROTOCOL=tcps
export TRIGGER_EDGEXMESSAGEBUS_PUBLISHHOST_PORT=8883
export TRIGGER_EDGEXMESSAGEBUS_OPTIONAL_AUTHMODE=clientcert
Use Node-Red to Connect to the TLS-enabled Edge Xpert Message Bus
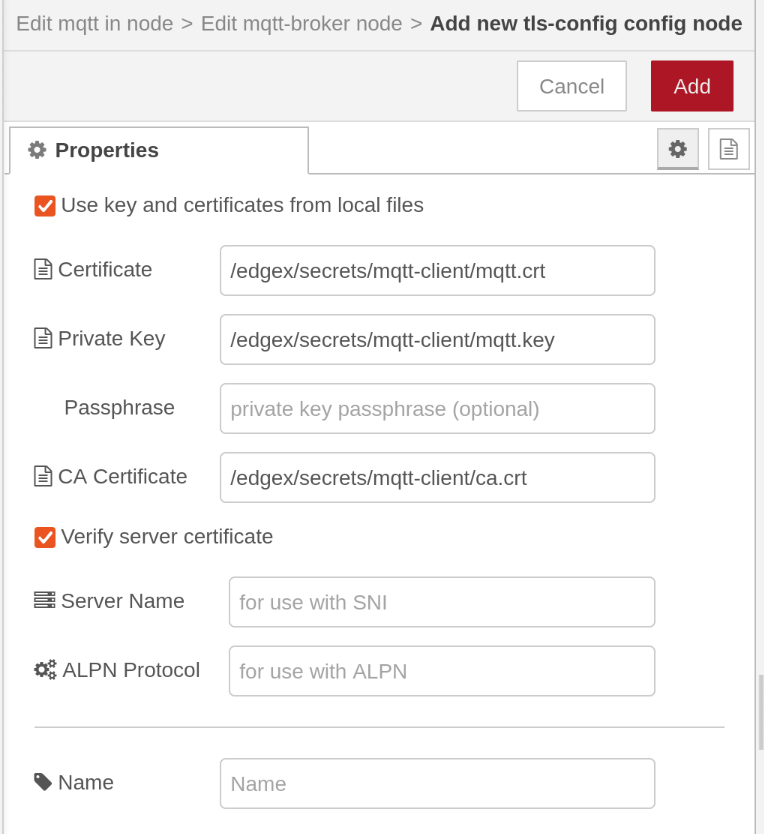
The key and certificate for the TLS connection are located at /edgex/secrets/mqtt-client inside the container:
-
Certificate: /edgex/secrets/mqtt-client/mqtt.crt
-
Private Key: /edgex/secrets/mqtt-client/mqtt.key
-
CA Certificate: /edgex/secrets/mqtt-client/ca.crt
To create an MQTT node with the key and certificate, select "Use key and certificates from local files" and enter the above file paths when adding tls-config to the MQTT node.