ONVIF User Authentication
To access the camera requiring authentication, you need to define the SecretPath. The secret data should contain:
username: the username of camera accountpassword: the password of camera accountmode: the camera's auth mode, the available values are "digest", "usernametoken", "both", "none"
Set Up the Default SecretPath
The SecretPath sets the default credentials to be used by devices that do not have defined MAC addresses or credentials defined in the CredentialsMap.
If "NoAuth" is used here, devices will default to using no authentication.
You can change the default secretPath by overriding the docker-compose file:
version: '3.7'
services:
device-onvif-camera:
environment:
APPCUSTOM_DEFAULTSECRETPATH: MyCredential
After deploying Edge Xpert in secret mode with the following command:
edgexpert up --secret device-onvif-camera
Inspect the IP of the device service:
docker inspect --format='{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' device-onvif-camera
172.20.0.9
Post the secrets into the secret store via the REST API of device service:
curl --request POST 'http://172.20.0.9:59985/api/v2/secret' \
--header 'Content-Type: application/json' \
--data-raw '{
"apiVersion":"v2",
"path": "MyCredential",
"secretData":[
{
"key":"username",
"value":"admin"
},
{
"key":"password",
"value":"admin"
},
{
"key":"mode",
"value":"usernametoken"
}
]
}'
Set Up Multiple SecretPaths
If there are multiple devices requiring different usernames and passwords, you can set up the CredentialsMap for mapping the SecretPath to the specified camera via MAC addresses.
Follow the below steps to set up the CredentialsMap with Edge Xpert:
Note
For Edge Xpert 2.3, Edge Xpert uses Core Keeper by default as its reference implementation configuration and registry providers. See Config & Registry for details.
-
Update CredentialsMap
We must use Core Keeper or Consul here as CredentialsMap is a map. It is not possible to override maps with docker-compose files.
-
Use Core Keeper
i. Deploy Core Keeper
ii. Create New SecretPathsedgexpert up --secret device-onvif-cameraexport KEEPER_HOST=`docker inspect --format='{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' core-keeper`# create MySecret01 curl http://$KEEPER_HOST:59890/api/v2/kvs/key/edgex/devices/2.0/device-onvif-camera/AppCustom/CredentialsMap/MySecret01 -X PUT -d '{"value":"aa:bb:cc:dd:ee:ff"}' # create MySecret02 curl http://$KEEPER_HOST:59890/api/v2/kvs/key/edgex/devices/2.0/device-onvif-camera/AppCustom/CredentialsMap/MySecret02 -X PUT -d '{"value":"02:42:D2:43:C7:FC,ff:ee:dd:cc:bb:aa"}' -
Use Consul
i. Deploy Consul
ii. Browse the Consul and add mapping to theedgexpert up --secret --no-core-keeper consul device-onvif-cameraAppCustom.CredentialsMap
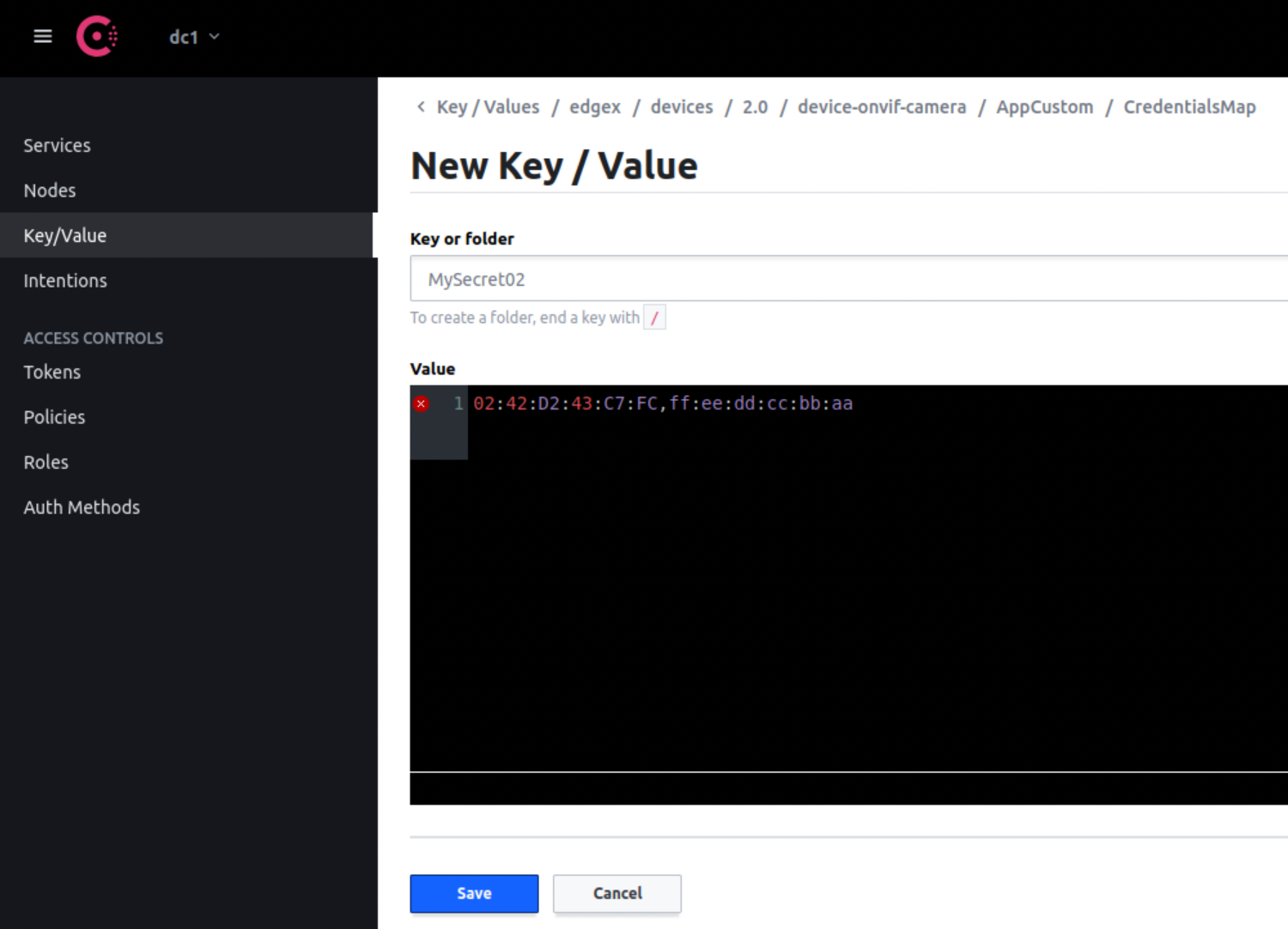
-
-
Confirm the configuration in the device service
$ curl http://172.20.0.9:59985/api/v2/config ... { "apiVersion" : "v2", "serviceName" : "device-onvif-camera", "config" : { ... "CustomConfiguration" : { "AppCustom" : { "BaseNotificationURL" : "http://192.168.12.112:59984", "CheckStatusInterval" : 30, "CredentialsMap" : { "MySecret01" : "aa:bb:cc:dd:ee:ff", "MySecret02" : "02:42:D2:43:C7:FC,ff:ee:dd:cc:bb:aa", "NoAuth" : "" }, ... } }, ... } } -
Post the secrets into the secret store via device service REST API:
curl --request POST 'http://172.20.0.9:59985/api/v2/secret' \ --header 'Content-Type: application/json' \ --data-raw '{ "apiVersion":"v2", "path": "MySecret02", "secretData":[ { "key":"username", "value":"admin" }, { "key":"password", "value":"admin" }, { "key":"mode", "value":"usernametoken" } ] }'
Note
- AppCustom.CredentialsMap is a map of SecretPath -> Comma separated list of MAC addresses
- Other MAC address not defined here will be assigned the default credentials configured via
DefaultSecretPath.